In my previous post, I talked about Stuxnet’s file hiding capabilities. In this post, I will cover the exact rules it follows to hide the files. Two of the files that Stuxnet hides are its payload files: “~WTR4132.tmp” and “~WTR4141.tmp”. These files come preloaded on an infected USB drive, and contain executable code which extracts the rest of the malicious code and installs it in the system.
The rules for mrxnet’s “.tmp” file hiding are as follows:
- Name must be prefixed by “~WTR”
- Name must have suffix “.TMP”
- Name must be exactly 12 characters long
- The sum of the 4 digits between the prefix and suffix of the name must be evenly divisible by 10.(sum%10 == 0)
- Filesize must be >= 4KB
- Filesize must be <= 8MB
NOTE: all the strings in the above rules are case insensitive-mrxnet converts all filenames to uppercase before evaluating its rules.
I found these rules using a combination of reading the disassembly, debugging the execution of the rules, and behavioral analysis. Below, we can see some of these rules implemented in the malware’s code:
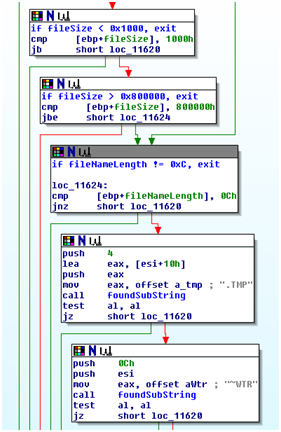
Implementation of file hiding rules in Stuxnet
In the above screenshot, we can see that the function I named “foundSubString” is called. This function seems to be logically equivalent to “!strncmp”. It returns 1 if the string matches and 0 otherwise. I am guessing the programmers decided not to call any of the kernel-provided string manipulation functions(remember, the standard userspace assumptions and APIs are not available when running in the kernel) in order to make the malware harder to reverse engineer.
By: Neil Sikka
