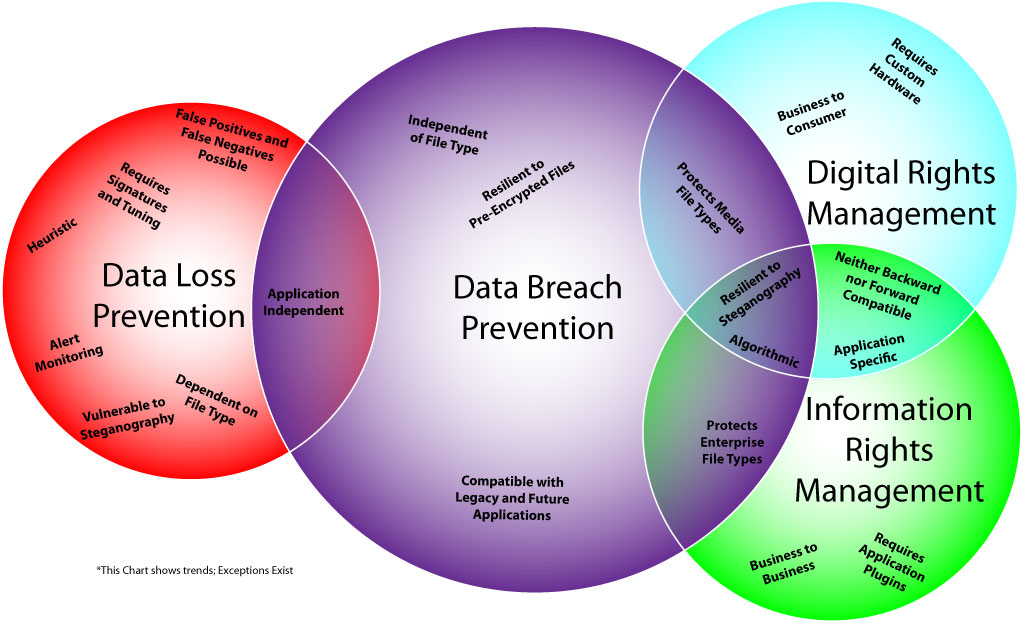
 With A1FILO, we have created a new breed of data protection product called Data Breach Prevention (DBP), which is neither DLP, IRM nor DRM, yet has some of the valuable characteristics of all three at the same time. To help clarify the different types of data protection software, we have defined each of the major categories and their differences below:
With A1FILO, we have created a new breed of data protection product called Data Breach Prevention (DBP), which is neither DLP, IRM nor DRM, yet has some of the valuable characteristics of all three at the same time. To help clarify the different types of data protection software, we have defined each of the major categories and their differences below:
- Data Breach Prevention (DBP) STOPS data breaches regardless of the application, file type or file format that it is protecting, without any heuristics. Application independence allows DBP to protect both legacy applications and future applications that the DBP vendor does not know about. DBP software requires no vendor knowledge of the application, which means there are no plugins for, or modifications to the software. In addition, DBP does not require any type of heuristics (scanning or detection), precluding the possibility of Steganography bypassing detection, false positives, false negatives or expensive human time spent analyzing alerts. DBP uses algorithms rather than heuristics, and therefore cannot be bypassed by Steganography. DBP is a mix of the functionalities of IRM, DRM and DLP.
- Information Rights Management (IRM) requires modification to the software it is protecting. For example, a Spreadsheet application or Word Processing application would require a plugin to support and enforce IRM. This design does not generalize to protect all applications an organization might run, because only applications that the IRM vendor knows about and builds plugins for, can be protected. For example, custom built legacy applications such as Computer Aided Design or Manufacturing (CAD/CAM) software, accounting software or health record software would not be protectable by IRM solutions. IRM is also not compatible with future applications because the IRM vendor would need to know about the application in order to build plugins for it. IRM is often a Business-to-Business security scheme.
- Digital Rights Management (DRM) is similar to IRM in that it requires special software, but additionally might also require special hardware that is aware of the protection scheme. DRM is associated with digital media content such as audio, video or games and does not protect files from off-the-shelf software that is run in enterprises. Video game consoles, handheld media players and set top boxes often implement DRM in hardware and software to stop piracy. DRM is often a Business-to-Consumer security scheme.
- Data Loss Prevention (DLP) tries to detect “sensitive” data (heuristics) before it leaves the organization. The difficulty with heuristic-based techniques that attempt to detect all the possible “sensitive” data in an organization, is that the term “sensitive” might not even be defined and agreed upon by an organization’s IT Administrators. Any type of heuristic detection can be trivially defeated by Steganography, the practice of encoding data to “hide in plain sight”. As a result, DLP only stops “the good guys” from accidentally breaching data, but does nothing to stop Malicious Insiders or Malicious Outsiders. Additionally, DLP produces alerts which human analysts have to investigate. DLP can be broken down into a few sub-categories:
- Network Data Loss Prevention (DLP) scans network traffic for “sensitive” content. Some products perform Man-In-The-Middle (MITM) network inspection to scan network traffic. Scanning of encrypted traffic is severely limited to applications that can, for example, work with a MITM on an SSL/TLS session (assuming scanning server’s certificates are trusted by the endpoint). Other than SSL/TLS sessions that can be MITM’ed, encrypted traffic cannot usually be scanned. Network DLP can be trivially defeated by Steganography.
- Host Data Loss Prevention (DLP) scans files that are being read or written on a host for “sensitive” content. Data encrypted by applications before being written cannot be scanned. This type of DLP is dependent on the file type, so that it can correctly parse the file and scan. Host DLP can be trivially defeated by Steganography.
- Discovery Data Loss Prevention (DLP) scans for “sensitive” data on various servers, computers, databases, websites, emails etc. Encrypted content cannot be scanned. Organizations often want to discover data in order to figure out what they need to protect, but the safer option is to protect everything in an organization and just let out certain files that need to be shared. It’s the general idea of being “secure by default, and being less secure by exception”. Discovery DLP can be trivially defeated by Steganography.
|
|
DBP |
IRM |
DRM |
DLP |
|
Protects Unmodified Applications |
X |
|
|
X |
|
Uses Algorithms |
X |
X |
X |
|
|
Backward and Forward compatible with legacy and future applications |
X |
|
|
X |
|
Stops Steganography |
X |
X |
X |
|
|
Works with any file format & file type |
X |
|
|
|
|
Resilient to false positives and false negatives |
X |
X |
X |
|
|
Supports enterprise file types (not just media files) |
X |
X |
|
X |
Steganography: Can your DLP Detect This?
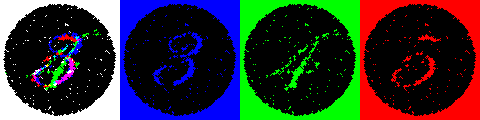
Example 1 Steganography defeats DLP
“The numerical identifier of the plastic format of transferring economic value is one hundred twenty three, followed by forty fore less than half the number of grams in a kilogram, followed by the greatest three single digit Arabic numerals, in order.”
Example 2 Steganography in text to bypass DLP detections

Example 3 Blurry captcha images cannot be scanned by DLP
A1FILO is the first Data Breach Prevention product in the industry. It protects any file type, file format and application without needing knowledge of what it is protecting. Also, it is algorithmic rather than heuristic, making it resilient to Steganography. The fact that it’s algorithmic precludes false positives, false negatives and tuning normally associated with DLP.
