In the development of sample exploit code for this blog (for example the Buffer Overflow post), various Windows attack mitigations had to be enabled or disabled. Two very effective and common mitigations on Windows 7 are DEP and ASLR. In an effort to save the reader frustration, time and effort, the compiler and linker options used to disable DEP and ASLR both independently and together are listed below. The DEP and ASLR columns of Mark Russinovich’s popular “Process Explorer” tool are used to determine whether a process has DEP or ASLR enabled.
Disable DEP
First, run “%windir%\system32\SystemPropertiesPerformance.exe” from the commandline, and select the “Data Execution Prevention” tab. Select the second option and specify which application to remove DEP protection for.
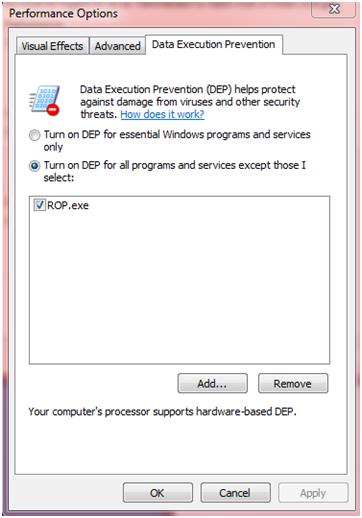
Opting out of DEP
In this case, ROP.exe was the executable for which DEP was to be disabled. Next, these are the commandline arguments to compile ROP.c without DEP:
cl ROP.c /GS- /Gs- editbin ROP.exe /NXCOMPAT:NO
ocess Explorer shows DEP as disabled for this process:
![]()
Disable ASLR
Commandline Arguments:
cl ROP.c /DYNAMICBASE:NO /link /FIXED
Now Process Explorer shows ASLR as Disabled for this process:
![]()
![]()
Disable both DEP and ASLR
Commandline Arguments:
cl ROP.c /DYNAMICBASE:NO /GS- /Gs- /link /FIXED editbin ROP.exe /NXCOMPAT:NO
![]()
The ability to selectively disable different mitigation techniques allows us to build smaller and less complex binaries, and makes it easier to perform static analysis and demonstrate security concepts. However, it is highly recommended to enable these mitigation technologies when building production binaries, as these mitigations greatly increase the security of the resulting binaries.
By: Neil Sikka
